Retail FX broker FBS was found to have left an unsecured ElasticSearch server containing almost 20TB of data and over 16 billion records, including very sensitive data.
The server was left open without any password protection or encryption and accessible to anyone. The major data breach was found by a team of white hackers from WizCase led by Ata Hakcil.
“The breach is a danger to both FBS and its customers. User information on online trading platforms should be well secured to prevent similar data leaks”, said Chase Williams, a web security expert at WizCase.
The data from FBS.com and FBS.eu comprised millions of confidential records including names, passwords, email addresses, passport numbers, national IDs, credit cards, financial transactions, and more.
The white hat team discovered the leak on October 1st, 2020, and reached out to FBS on October 2nd. Subsequently, FBS secured the server on October 5th.
“Were such detailed personally identifiable information (PII) to fall in the wrong hands, it could have been used in the execution of a wide range of cyber threats. The data leak was unearthed as part of WizCase’s ongoing research project that randomly scans for unsecured servers and seeks to establish who are the owners of these servers. We notified FBS of the breach so they could take appropriate action to secure the data”, Williams added.
FBS has more than 400,000 partners and 16 million traders spanning over 190 countries. The FBS app for the Android OS has been downloaded more than one million times on Google Play Store as of January 2021.
According to the retail broker, which is an official trading partner of soccer giants FC Barcelona, FBS clients rake in half a billion dollars in profit each year.
Nearly 20TB of data was leaked comprising more than 16 billion records. Millions of FBS users spread across the world were affected.
Sensitive information included names and surnames, email addresses, Phone numbers, Billing addresses, Country, Time zone, IP addresses, Coordinates, Passport numbers, Mobile device models, Operating system, Email sent to FBS users, Social media IDs including GoogleIDs and FacebookIDs, Files uploaded by users for verification including personal photos, national ID cards, drivers licenses, birth certificates, bank account statements, utility bills, and unredacted credit cards.
User ID and Credit Card Photo Uploads


User details such as
- FBS user ID
- FBS account creation date
- Unencrypted passwords encoded in base64
- Password reset links
- Login history
- Loyalty data including loyalty level, level points, prize points, total money deposited, active days, active clients, points earned and points spent
A German User’s Account

An Australian User’s Account
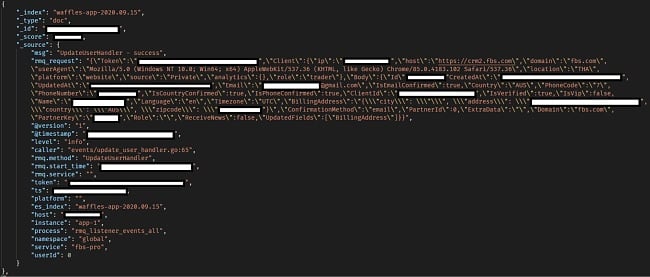
Plain Text (base64) Passwords
Financial details such as
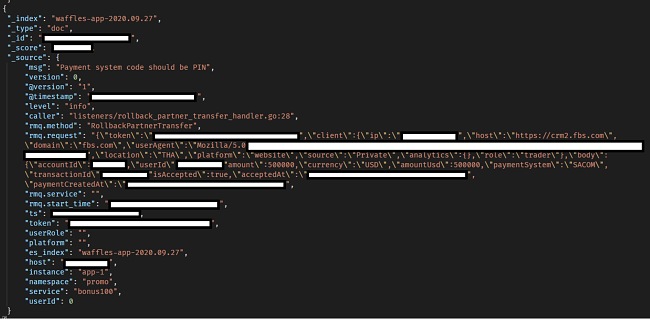
- User transaction details including deposited money, currency, payment system, transaction IDs, account IDs, transaction dates, number of times money was deposited, last deposit amount, last deposit date, total deposit, credit, balance, last month’s balance, interest rate, taxes, equity and margin free. Some of the transactions are really large.
A $500,000 Transaction
Each data set would on its own provide valuable information for an attacker but combining all of them makes the threat much more formidable.